Access Control Configuration
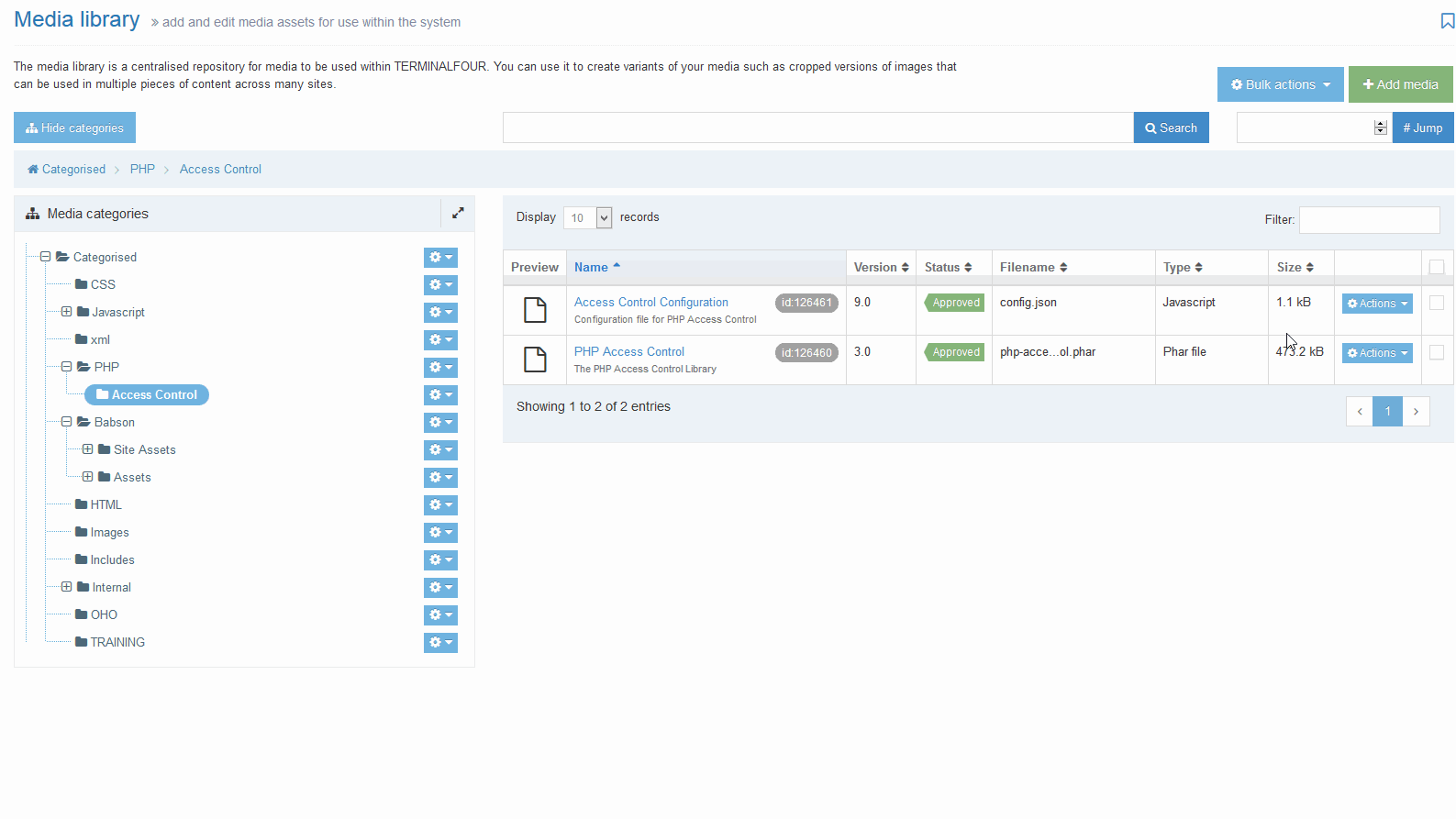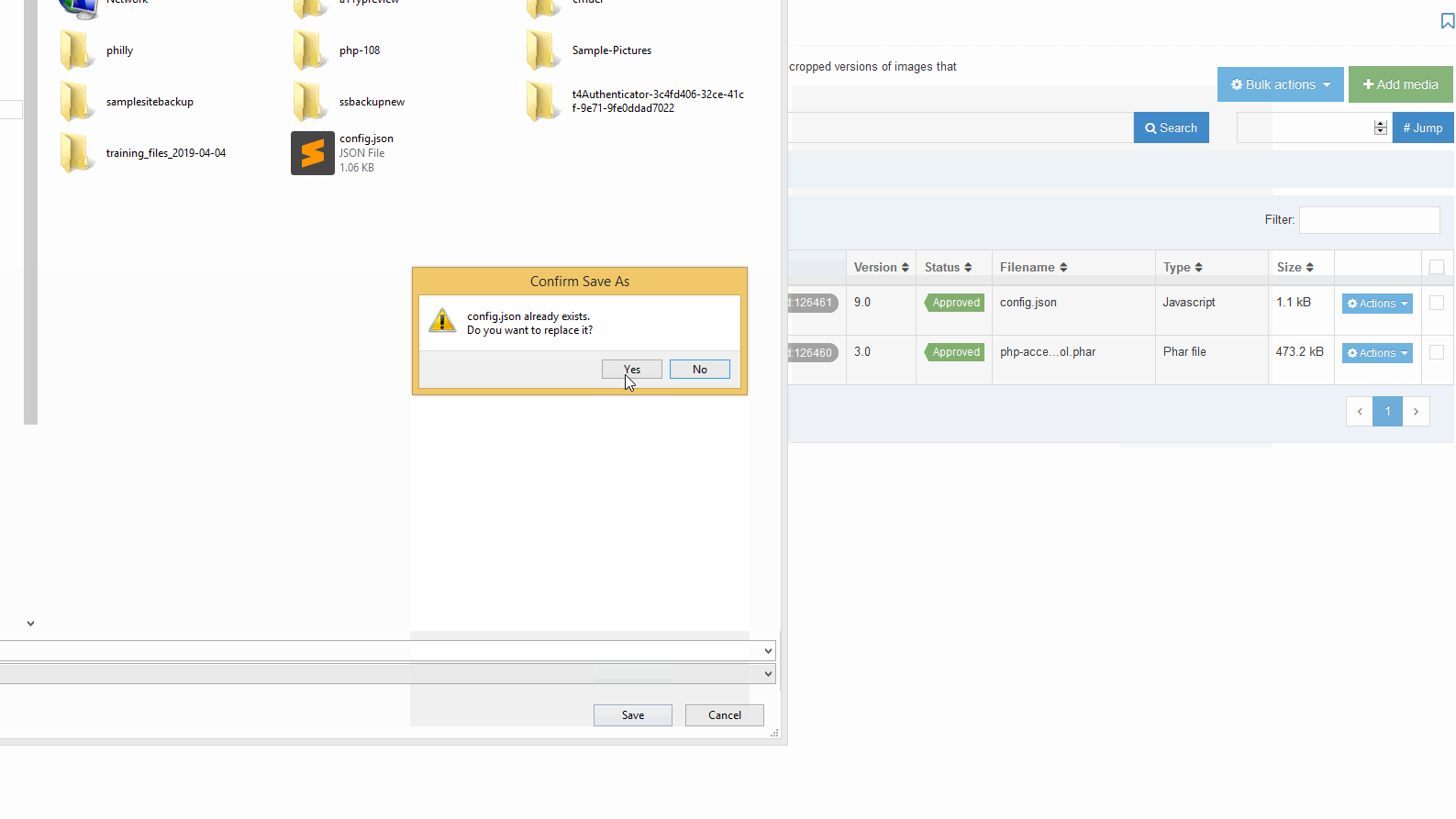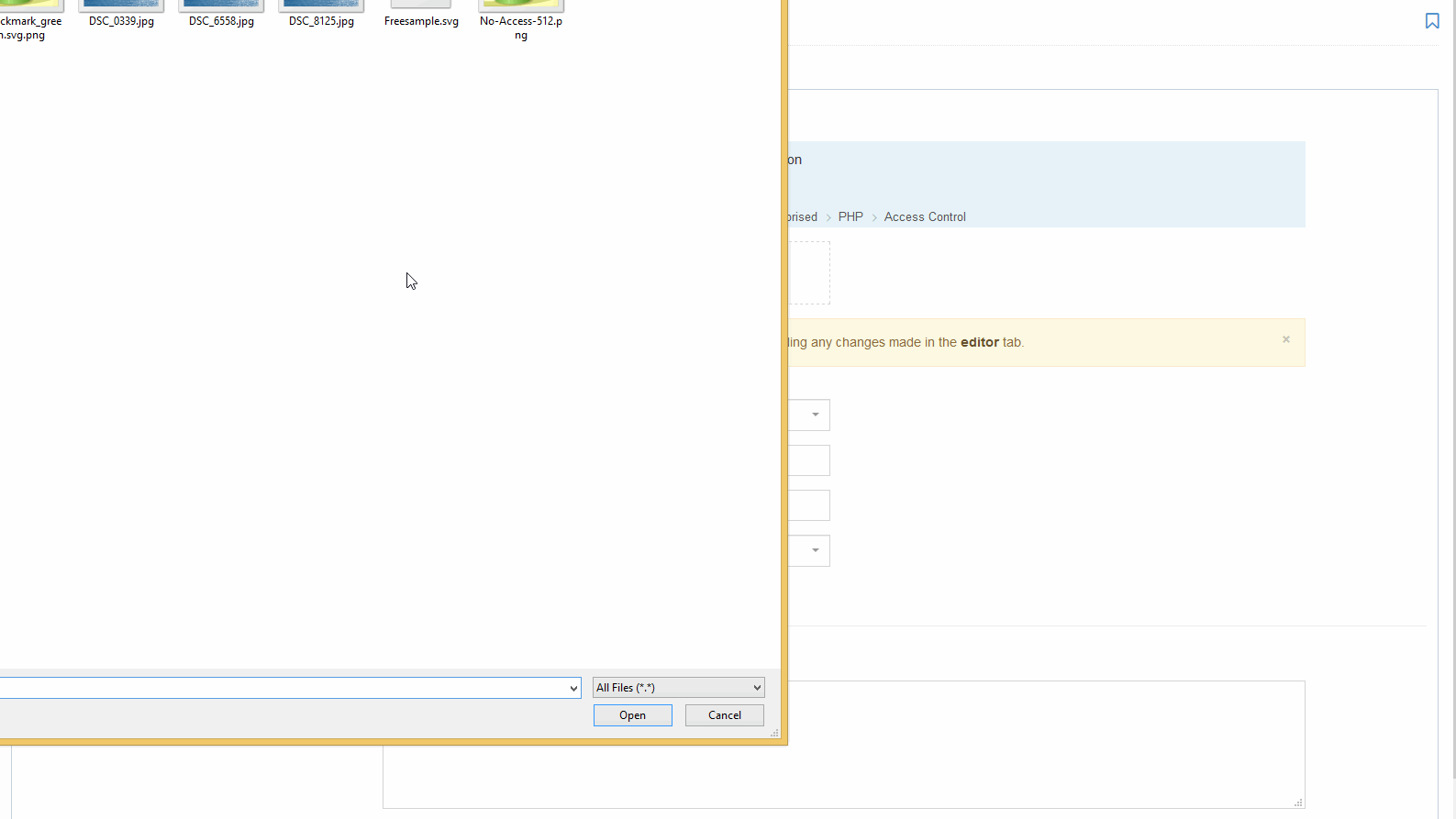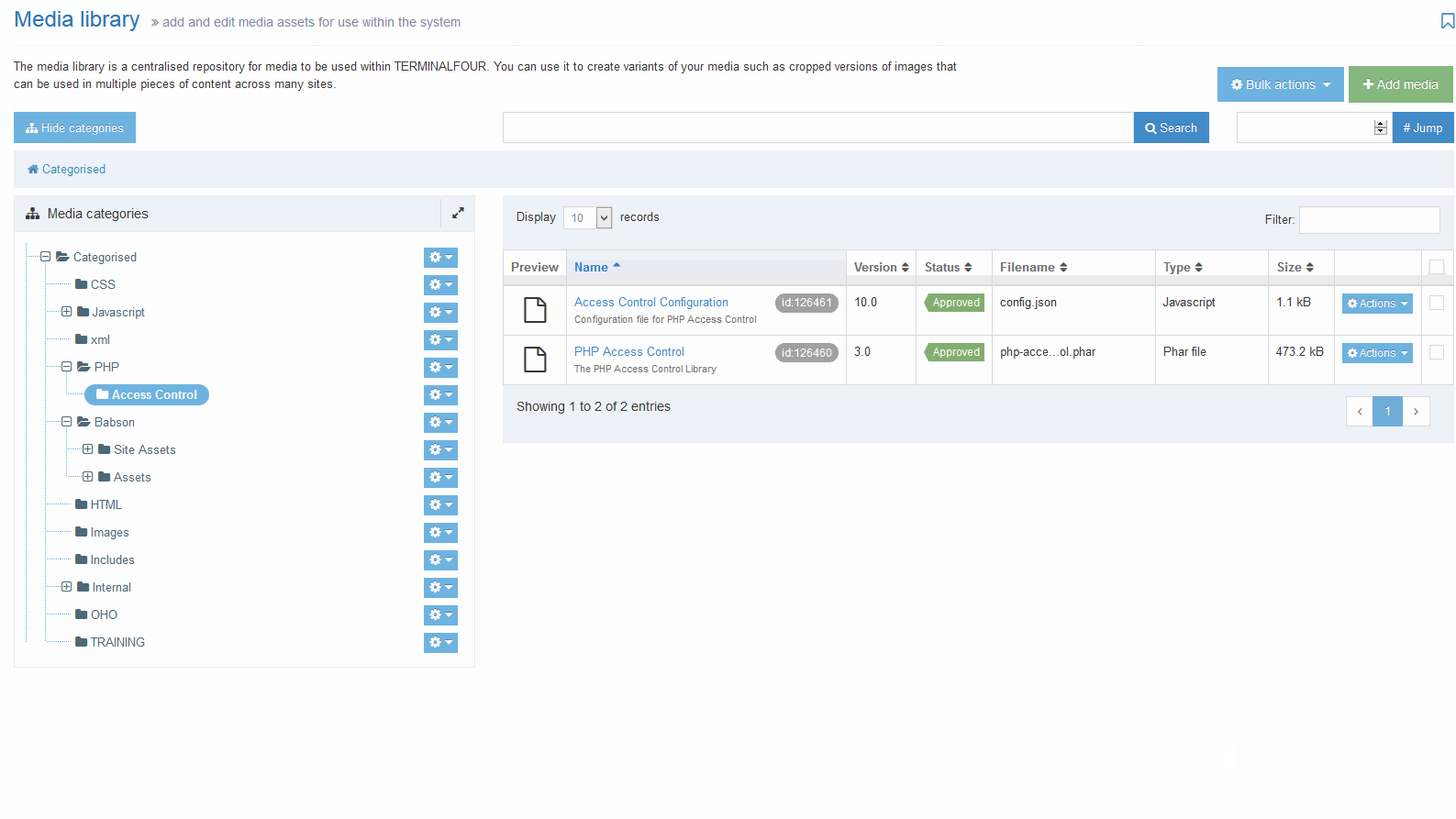
When you have installed the PHP Access Control module, you can configure the default settings. The PHP Access Control Configuration is a JSON file that's located in the Media Library. The Media Category that it uses will have been chosen on installation. Omitted configurable options will revert to the default values that are documented below.
Updating the PHP Access Control Configuration file
The file can be updated by navigating to the appropriate Category in the Media Library and locating the Access Control Configuration JSON file. It will generally be named "Access Control Configuration"' but this can be customized on install. This file can be edited in two ways:
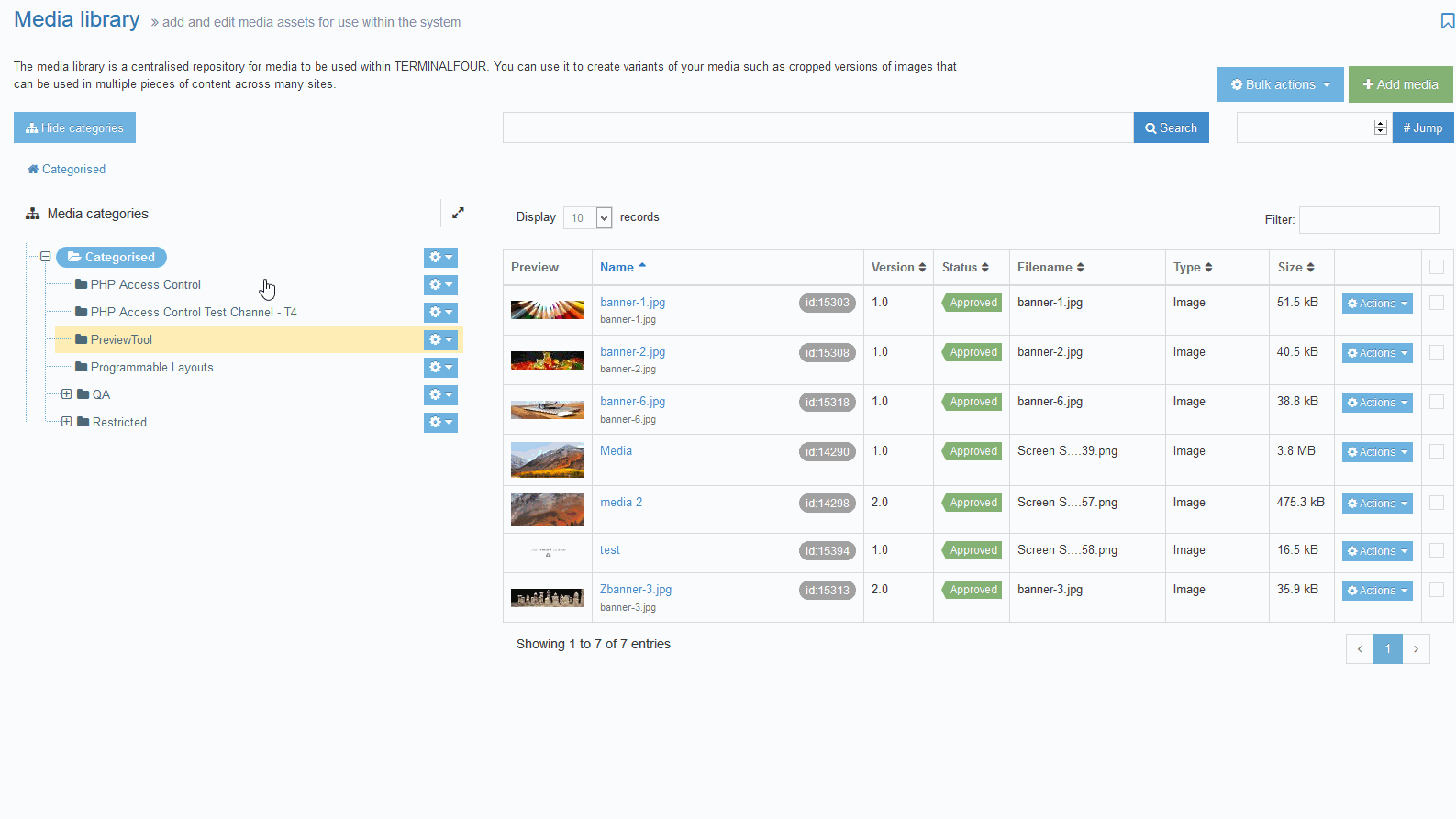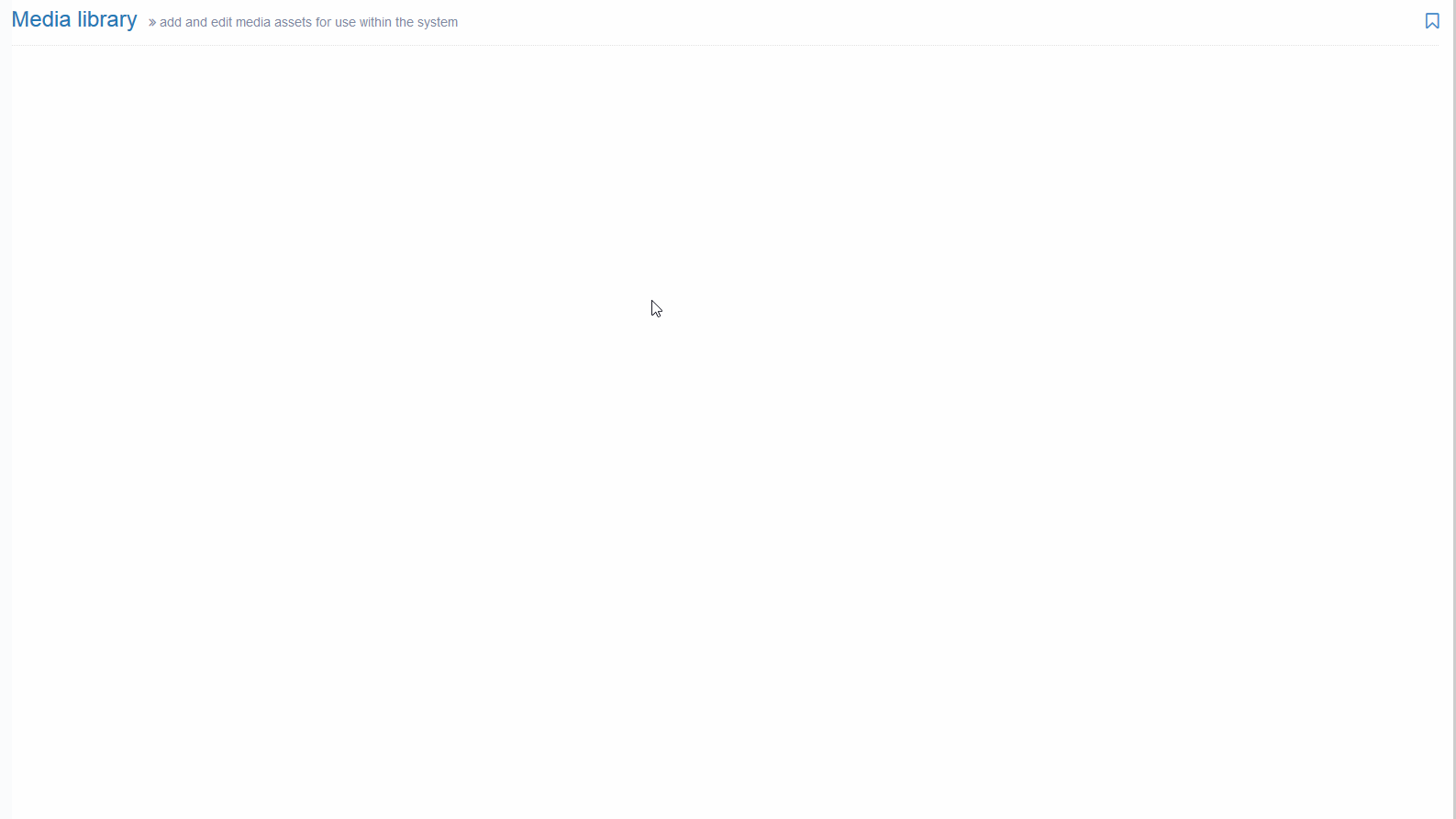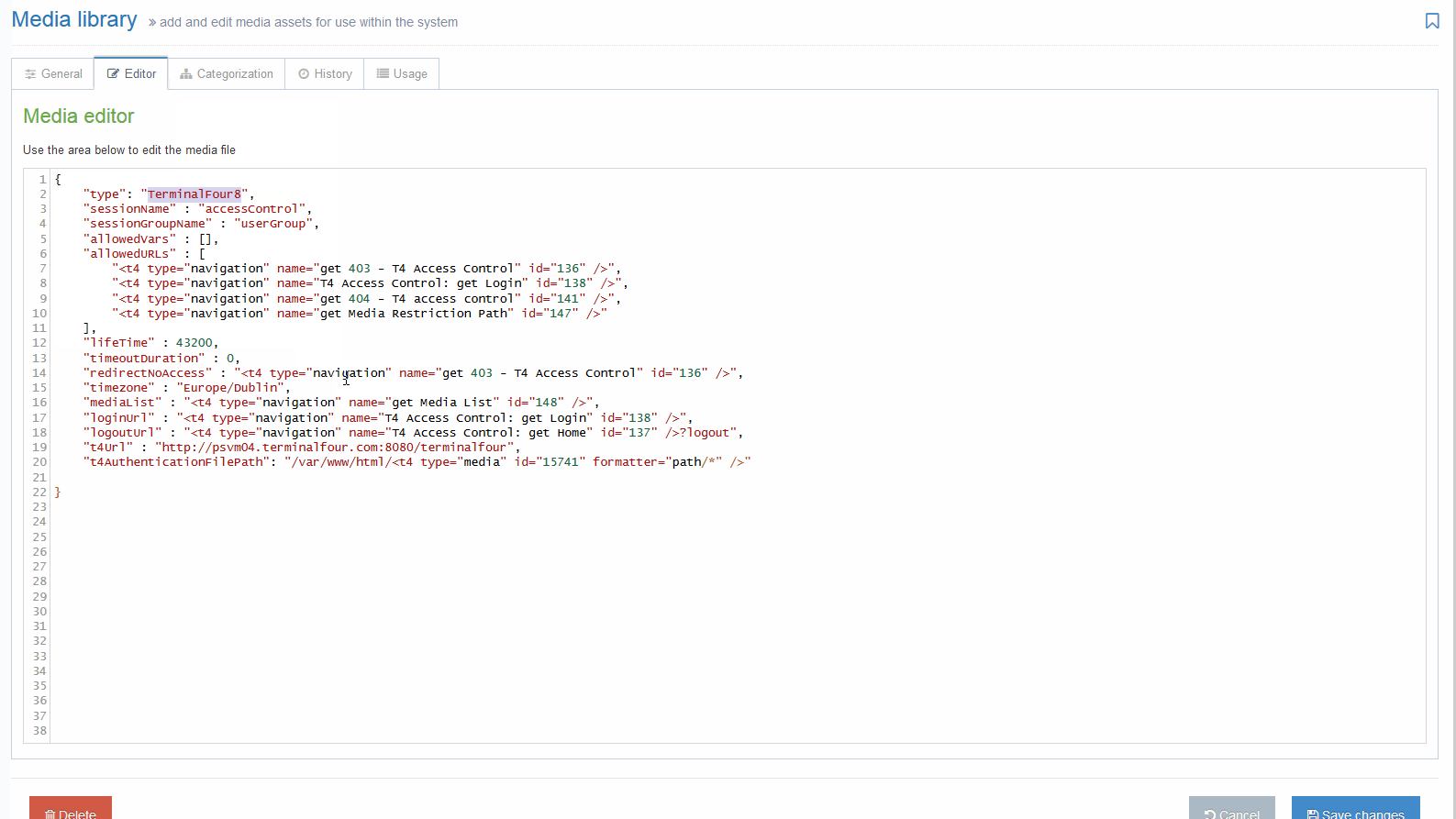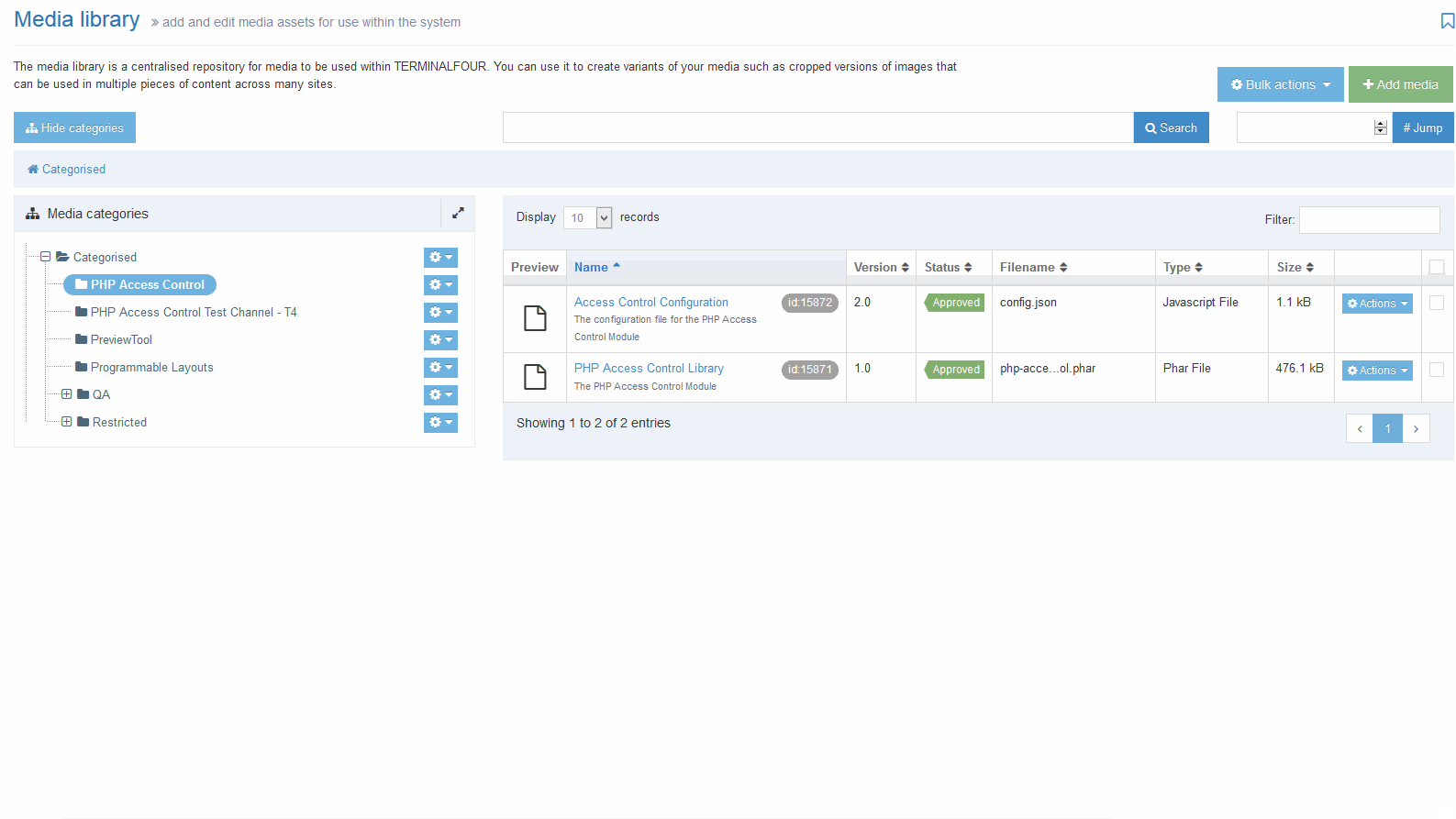
1. Via the "Editor" tab in the Media Library after selecting the file. This tab is only visible if the file type is not marked as binary in the settings:
2. Downloading the file, and re-uploading the updated file when changes have been made:
It is recommended that the JSON configuration files contents are passed through a JSON validator prior to updating or uploading to avoid configuration errors. Errors surrounding the use of double quotes in T4 Tags can safely be ignored as the contents will be replaced on publish.
Supported Settings
The following keys, when added to the Access Control Configuration file are recognized by the PHP Access Control Module:
| Key | Value Format | Description | Required (If of supported Type | Supported By Access Control Type | Default | ||
|---|---|---|---|---|---|---|---|
| type | String | The Type of access control (one of "Cas", "Variables", "Terminalfour8") | Yes | CAS | Server Variables | TERMINALFOUR | "Variables" |
| sessionName | String | The Name of the PHP Session | Yes | CAS | Server Variables | TERMINALFOUR | "accessControl" |
| sessionGroupName | String | The name of the environment variable containing group info. For SAML it needs to match the name of the server variable containing groups. | Yes | Server Variables | "role" | ||
| allowedVars | array[String] | A list of the variable names that can be accessed by the module | CAS | Server Variables | TERMINALFOUR | ["emailaddress", "givenname", "surname", windowsaccountname"] | |
| allowedIps | array[String] | A list of IPs and IP ranges that should be whitelisted. Ranges should be in the from IP/to IP format - subnet masks are not supported. |
CAS | Server Variables | TERMINALFOUR | [] | |
| loginUrl | String | The relative URL for the login page. For Terminalfour authentication it should point to the login section. For SAML it will usually be /Shibboleth.sso/Login |
Yes | CAS | Server Variables | TERMINALFOUR | "/" |
| usernameVarName | String | The name attribute of the field for username in login form | Yes | CAS | TERMINALFOUR | "uname" | |
| passwordVarName | String | The name attribute of the field for password in login form | Yes | CAS | TERMINALFOUR | "pwd" | |
| logoutUrl | String | The URL that triggers the logout process. For Terminalfour authentication it should be /path/to/login?logout. For SAML it will usually be /Shibboleth.sso/Logout |
Yes | CAS | TERMINALFOUR | "?logout" | |
| allowedUrls | array[String] |
An array of URLs for which access control rules are bypassed (e.g. for 404 pages). Usually it should contain the login page, the logout page, the no access page and the media restriction section |
CAS | Server Variables | TERMINALFOUR | ["/400", "/401", "/403", "/404", "/405", "/407", "/408", "/500", "/502", "/503", "/504"] | |
| groupRedirects | array(Key => Value) | An array of key value pairs, used to assign urls to a particular group in order to redirect users of that group to the url. These rules are applied in order of appearance with the first rule in the array taking precence in the case of multiple matching groups (e.g. a rule of "admin"=>"/account" will result in members of the group admin being redirected to the /account page. | CAS | Server Variables | TERMINALFOUR | [{"groupA" : "urlA"}] | |
| redirectSources | array(String) | An array of urls from which the rules defined in the groupRedirects key will be applied | CAS | Server Variables | TERMINALFOUR | ["sourceUrlA"] | |
| clientSecure | boolean | If True, Cookie will only be sent over secure connections (https) | CAS | Server Variables | TERMINALFOUR | false | |
| httpOnly | boolean | If True, httponly flag will be set on session cookie | CAS | Server Variables | TERMINALFOUR | true | |
| lifeTime | Integer | sets the maximum duration of the session. | CAS | Server Variables | TERMINALFOUR | 43200 | |
| timeoutDuration | Integer | sets the number of seconds after which to expire the session when there is no interaction | CAS | Server Variables | TERMINALFOUR | 3600 | |
| redirectNoAccess | String | The URL that the user will be redirected to if it is found that their group does not have access to the content | Yes | CAS | Server Variables | TERMINALFOUR | "/403" |
| timezone | String | Used to set the correct timezone that the server is located in | Yes | CAS | "Europe/Dublin" | ||
| casHost | String | The Domain at which the CAS service is accessed | Yes | CAS | "localhost" | ||
| casContext | String | The subdirectory for the CAS Service | Yes | CAS | "/cas" | ||
| casPort | Integer | The Port at which the CAS Service is accessible | Yes | CAS | 8443 | ||
| certificate | String | The absolute path (on the server) at which the certificate is located to enable secure connections | Yes | CAS | "" | ||
| t4AuthenticationFilePath | String | The Location of the file containing Credentials for the TERMINALFOUR instance specified in t4Url |
Yes (if t4Url is used) |
TERMINALFOUR | "" | ||
| t4Url | String |
The URL of the TERMINALFOUR Instance that you would like users to authenticate against |
Yes (At Least one of these two must be specified) |
TERMINALFOUR | http://samplesite.terminalfour.com | ||
| authenticatorUrl | String | The URL of the authentication service to use for t4Authentication | "" | "" | |||
| authenticatorKey | String | The Secret Key for the Authentication Service used in authenticatorUrl |
Yes (if authenticatorUrl is used) |
TERMINALFOUR | |||
| groupSplitRegex | String | Regular Expression (PCRE) to use to split the group environment variable into an array of groups | Yes | Server Variables | "" | ||
| groupSplitCharacterSequence | String | String used to split the String found in the group environment variable into an array of groups (will use groupSplitRegex if both this and groupSplitRegex are specified) | Yes | Server Variables | "" | ||
| mediaList | String | Pipe(|) separated list of rules used to limit access to media files e.g. "/secure/category/=admin|/secure/other/=student" will restrict contents of /secure/category to users with the admin group and contents of /secure/other to members of the student group. This should be generated by the Get All Media Restriction Rules navigation object. |
Yes (For media and file element access control) |
CAS | Server Variables | TERMINALFOUR | "" |
|
mimeType
|
Object | It is possible to specify additional mime types for Media Files. In order to properly access control media files a PHP snippet of code will output the content of the file of redirect to a login, if the mime type is not a default one may add a generic 'application/octet-stream' | No | CAS | Server Variable | Terminalfour | { "css": "text/css", "csv" : "text/csv", "doc" : "application/msword", "docx" : "application/vnd.openxmlformats-officedocument.wordprocessingml.document", "exe" : "application/octet-stream", "gif" : "image/gif", "htm" : "text/html", "html" : "text/html", "pdf" : "application/pdf", "txt" : "text/plain", "jpeg" : "image/jpg", "jpg" : "image/jpg", "js" : "application/javascript", "json" : "application/json", "php" : "text/plain", "png" : "image/png", "ppt" : "application/vnd.ms-powerpoint", "pptx" : "application/vnd.openxmlformats-officedocument.presentationml.presentation", "svg" : "image/svg+xml", "xls" : "application/vnd.ms-excel", "xlsx" : "application/vnd.openxmlformats-officedocument.spreadsheetml.sheet", "xml" : "application/xml", "zip" : "application/zip" } |